Have a Question?
coreboot Build Guide
Overview: Building coreboot
coreboot is an open source firmware project that can be used as an alternative BIOS that provides a faster and more secure booting process. The coreboot home page can be found at this link coreboot. More information on the security aspects and features for coreboot on all Vaults can be found at this link: https://kb.protectli.com/kb/coreboot-information/ This article describes how to build and flash coreboot using the Vault Pro VP4630 as an example. A list of supported platforms can be found in the table at the bottom of this article.
As an open source project, it is important to make code available for inspection and building. coreboot has an official "upstream" approval process, however, it requires a lot of time to process. This creates a long delay between the release of a product and the availability of coreboot binary and the source code to the general public. In order to expedite the availability of the source code to the general public, Protectli has devised a "build_coreboot" repository to expedite the release of the source code.
Open Source and "blobs"
In addition to the source code, there are binary modules that are also required. These modules are referred to as "blobs". Intel blobs are proprietary and some are only available to licensed users. As such, some Intel blobs are NOT included with the distribution of this source code and build instructions as Protectli does not have the rights to redistribute Intel proprietary blobs. To successfully build coreboot for the VP series, access to Intel blobs is required.
The blobs are listed below and are summarized in the following table.
ME firmware – Intel proprietary – an embedded coprocessor on some Intel processors that requires ME firmware to run.
Flash descriptor – not public – 4KB data structure on modern Intel platforms. The descriptor is not public but because it does not contain any code the distribution is not restricted.
Microcode – public – translates micro operational architecture and CPU state into machine instructions.
FSP – public – Firmware Support Package. Initializes Intel silicon.
Bootsplash – public – Splash screen image when the device boots. Any image can be used that does not break any copyrights or regulations, but must adhere to supported specifications for the unit.
VBIOS – not public – Legacy ROM for Intel GPUs. It is used for legacy boot devices. It does not apply to the VP2400 or VP4600 series as it's UEFI only.
VBT – public – Intel data structure that describes GPU configuration. FSP uses VBT to initialize UEFI systems.
The VP4630 is the first Protectli platform that has source code in the build_coreboot repository. This article will describe the process to acquire the VP4630 coreboot version v1.0.17 source code and build the files. The table below is specific to the VP4630.
Code Inspection
Even if one does not have access to the "blobs", inspection of the source code may be desirable.
Source code for version v1.0.17 for Protectli VP4630 coreboot is located at this link Protectli github VP4630 source code.
Source code for version v1.0.19 for Protectli VP4650 coreboot is located at this link Protectli github VP4650 source code.
Source code for version v1.0.15 for Protectli VP2410 coreboot is located at this link Protectli github VP2410 source code.
Build Guide: coreboot
The following build guide uses VP4630 build instructions as an example. Refer to the chart at the bottom for specific vault builds.
————————————————————————————————————————————————————
WARNING
WARNING: BUILDING WITHOUT THE PROPER INTEL BLOBS WILL RESULT IN A FAILED
BUILD AND WILL NOT PRODUCE A USABLE IMAGE.
CONTINUING THE FOLLOWING STEPS AND FLASHING WITH THE PRODUCED ROM IMAGE CAN "BRICK" THE DEVICE AND LEAVE IT INOPERABLE.
BUILD AND FLASH AT YOUR OWN RISK.
————————————————————————————————————————————————————
Prerequisites
Protectli recommends a fresh installation of Ubuntu 22.04 on the actual platform that will be the target machine. For Ubuntu installation instructions, see this link. How to install Ubuntu on the Vault Although it is possible to build coreboot in other Linux development environments, only Ubuntu 22.04 has been verified with Protectli coreboot. Internet access is required to download the dependencies and source code. The instructions below are for the Protectli VP4630.
Installing dependencies
"git" is required to obtain the source code from github.
Open a terminal in Ubuntu.
Shortcut to open the terminal:ctrl + alt + t
Install git using the following command:
#sudo apt install git
Verify that git is installed:
#which git
Obtain coreboot files
Obtain source code files from github by running the following command:
#git clonehttps://github.com/protectli-root/build_coreboot.git -b protectli_vp4630_v1.0.17
Verify the files have been downloaded:
#ls
Verify a new directory called "build_coreboot" is created.
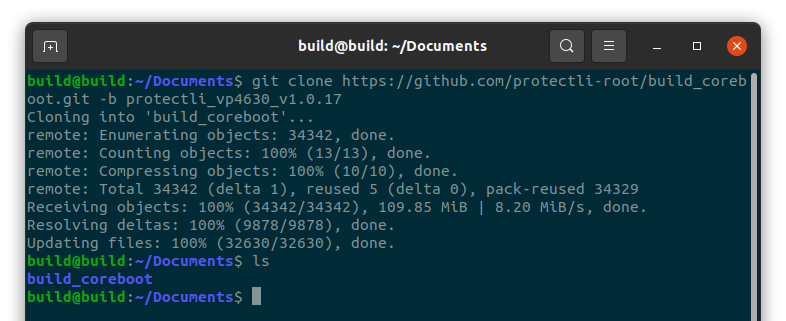
Change into the build directory:
#cd build_coreboot/
Verify that you are in the build_coreboot directory.
#ls
Verify a variety of files and folders including set_env.sh, build.sh and 3rdparty are displayed.
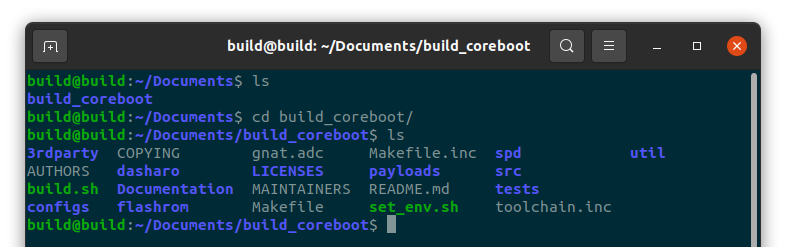
Verify the correct branch
#git status
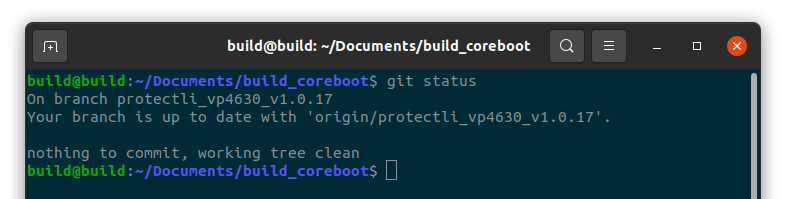
Verify you are in the proper branch for the device/version that you are building. If not, change to the correct branch.
For example, if you are building coreboot for the vp4630 v1.0.17:
#git checkout protectli_vp4630_v1.0.17
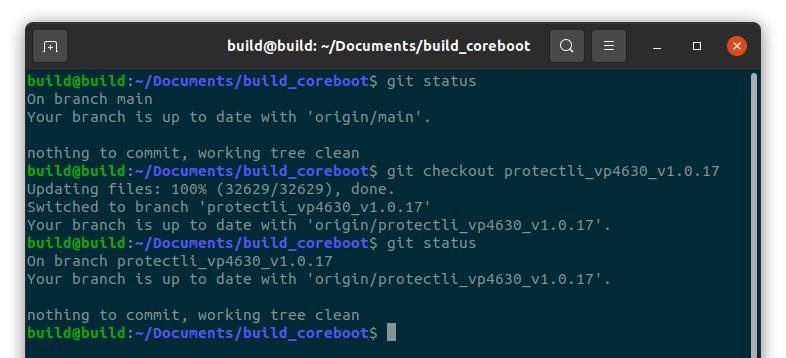
Obtain FSP modules
To obtain the Intel FSP modules run command:
#git submodule update --init --checkout
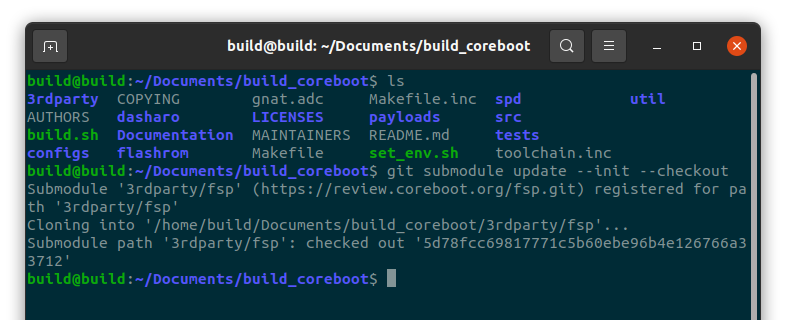
Verify that the fsp modules have been downloaded.
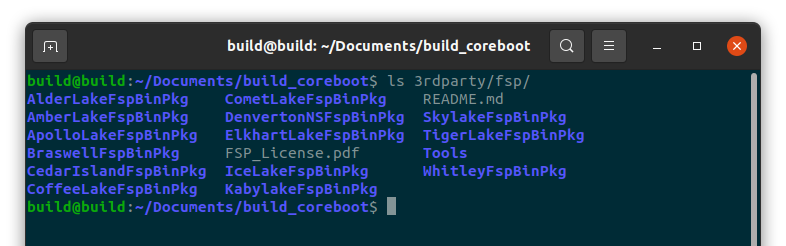
#ls 3rdparty/fsp/
Verify that the directory is populated.
Setup the coreboot Build Environment
Verify you are in the "build_coreboot" directory and run the following script to set up the environment:
#sudo ./set_env.sh
Verify that docker was installed:
#which docker
Verify that "/usr/bin/docker" is displayed.
Obtain blobs
Intel blobs are NOT included with the distribution of this source code and build instructions. They will need to be acquired separately.
You will need to insert the proper binary for Management Engine (ME) firmware into the source tree.
Once the ME binary is obtained, if it is not already named "me.bin", rename it to "me.bin".
Place the binary into the following directory:
build_coreboot/3rdparty/blobs/mainboard/protectli/vault_cml/
Verify that the binary was placed and named properly:
#ls 3rdparty/blobs/mainboard/protectli/vault_cml/
Building coreboot
The source tree is now ready to build coreboot.
Verify you are in the "build_coreboot" directory.
Run the following script to build coreboot:
#sudo ./build.sh
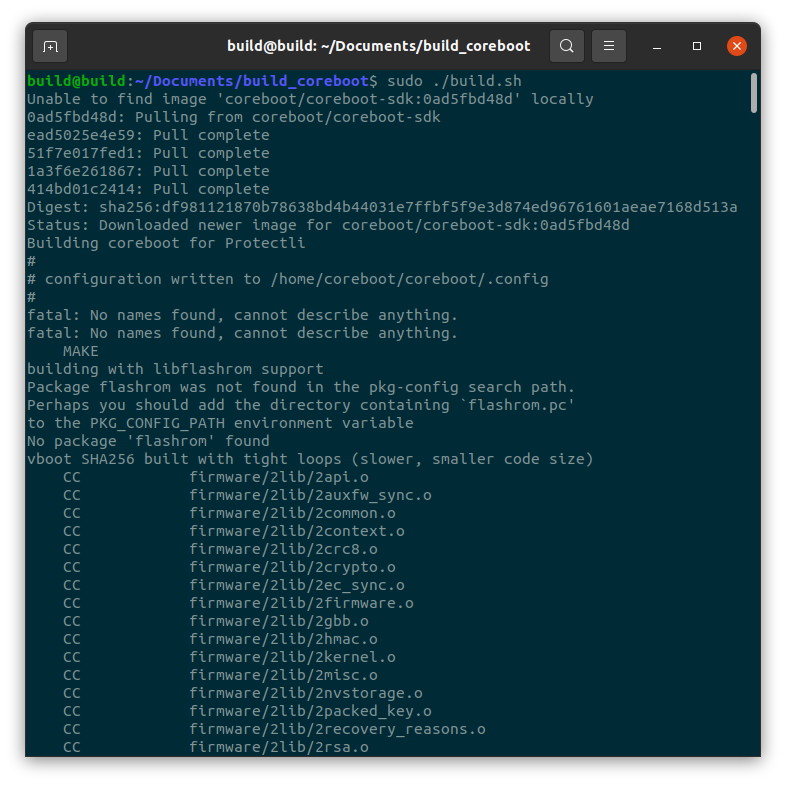
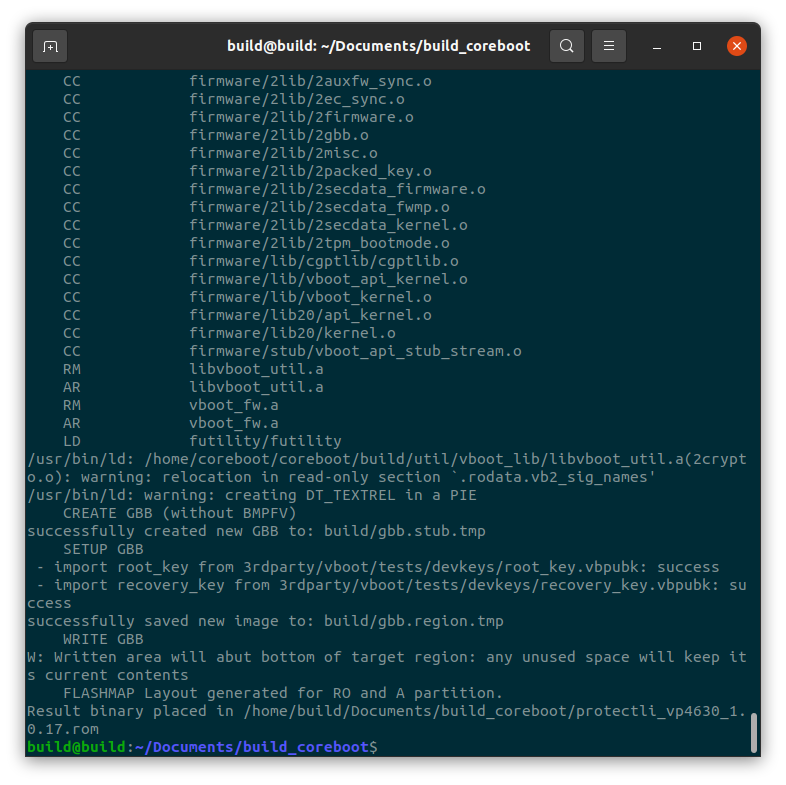
When the build is completed, verify the images are present by running the following command:
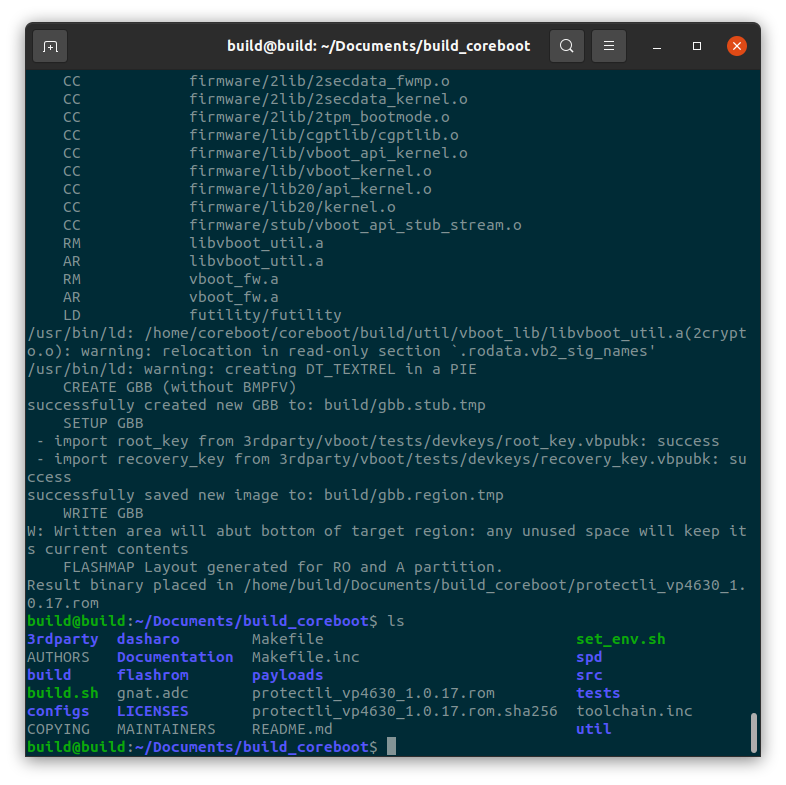
#ls
Verify protectli_vp4630_v1.0.17.rom and protectli_vp4630_v1.0.17.rom.sha files are displayed
Verify sha256sum
Run the following command on the .rom file to display the sha256sum of the coreboot image, VP4630 v1.0.17 example.
#sha256sum protectli_vp4630_v1.0.17.rom
The sha256sum of Protectli VP4630 v1.0.17 is 95cb4c9399997df4b8efcc6fc9fbd8762a749d5de0402158ceebcfa411b4b745
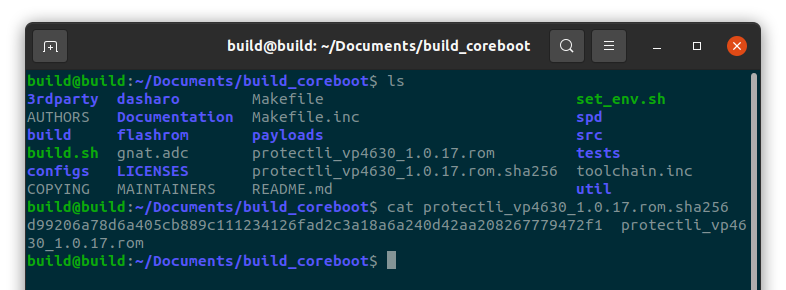
The sha256sum may be different based on the blob files that were used, as well as any other alteration made to the source code.
Flashing newly built coreboot.
Verify the BIOS Lock is disabled. If BIOS Lock is not disabled the flash will fail and could brick the device.
Reboot the device. While rebooting, press "DEL" to enter the BIOS menu.
In AMI, the BIOS Lock is located in Chipsets -> PCH-IO Configuration -> BIOS lock. If BIOS Lock is enabled, disable it. Save the changes, if needed, and reboot
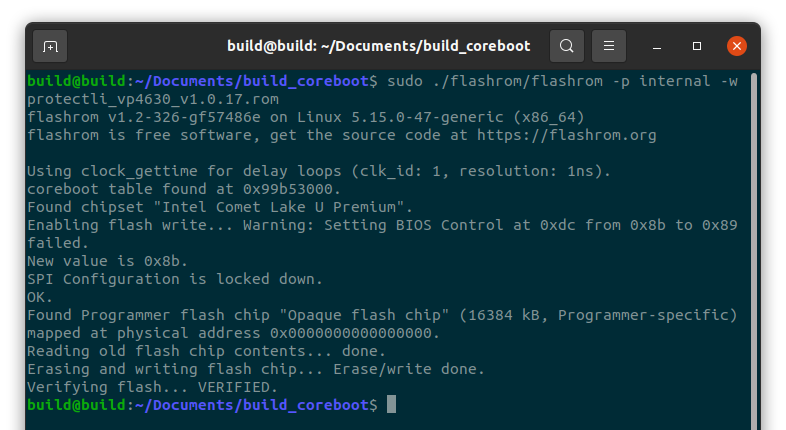
A known good flashrom binary has been provided in the build_coreboot package for flashing. Verify you are in the build_coreboot directory.
Run flashrom in sudo using the following command:
#sudo flashrom/flashrom -p internal -w protectli_vp4630_v1.0.17.rom
Verify that flashrom has successfully finished.
If the flash fails, do not power off the device. The BIOS chip will contain code from the image used to flash, however, it will not be executed until next boot. Try running the flashrom command again. If that does not work, to avoid bricking the device, use Flashli to flash back to a known good BIOS image. The Flashli tool can be found at this link flashli.
At this point, the newly built coreboot has been flashed to the Vault.
As always, if you experience any issues, please feel free to reach out: support@protectli.com.
Vault Reference Chart
VP2410 coreboot Components
| Components | Used in build | Source | Version | Notes |
|---|---|---|---|---|
| coreboot Version | Yes | Included in the build | 4.13 revision f59b1ec9 | |
| ME firmware | Yes | Proprietary - Not Included | Based on 4.0.30.1392 | |
| Flash Descriptor | Yes | Included in build | ||
| Microcode | Yes | Included in build | Extracted - has not tested with public microcode | |
| FSP | Yes | Proprietary-not included | GeminiLake | Prtectli version of GeminiLake FSP contains patches and bug fixes |
| Bootspalsh | Yes | Included in build | N/A | Protectli Splash Screen |
| Video BIOS | No | N/A | N/A | |
| Video boot table (VBT) | Yes | Included in build | ||
VP2420 coreboot Components
| Components | Used in build | Source | Version | Notes |
|---|---|---|---|---|
| coreboot Version | Yes | Included in the build | 4.18 revision e36a117d | |
| ME firmware | Yes | Proprietary - Not Included | Based on 2131.1.4.0 | |
| Flash Descriptor | Yes | Included in build | ||
| Microcode | Yes | Included in build | Intel Microcode | |
| FSP | Yes | Pulled from Intel github | ElkhartLake | Intel FSP |
| Bootspalsh | Yes | Included in build | N/A | Protectli Splash Screen |
| Video BIOS | No | N/A | N/A | |
| Video boot table (VBT) | Yes | Included in build | ||
VP4630 coreboot Components
| Components | Used in build | Source | Version | Links |
|---|---|---|---|---|
| coreboot Version | Yes | Included in the build | 4.16 revision d662831d | |
| ME firmware | Yes | Proprietary - Not Included | Based on 14.0.47.1558 | |
| Flash Descriptor | Yes | Included in build | ||
| Microcode | Yes | Included in build | Intel Microcode | |
| FSP | Yes | Pulled from Intel github | CometLake2 | Intel FSP |
| Bootspalsh | Yes | Included in build | N/A | Protectli Splash Screen |
| Video BIOS | No | N/A | N/A | |
| Video boot table (VBT) | Yes | Included in build | ||
VP4650 coreboot Components
| Components | Used in build | Source | Version | Links |
|---|---|---|---|---|
| coreboot Version | Yes | Included in the build | 4.16 revision d662831d | |
| ME firmware | Yes | Proprietary -Not Included | Based on 14.0.47.1558 | |
| Flash Descriptor | Yes | Included in build | ||
| Microcode | Yes | Included in build | Intel Microcode | |
| FSP | Yes | Pulled from Intel github | CometLake2 | Intel FSP |
| Bootspalsh | Yes | Included in build | N/A | Protectli Splash Screen |
| Video BIOS | No | N/A | N/A | |
| Video boot table (VBT) | Yes | Included in build | ||
VP4670 coreboot Components
| Components | Used in build | Source | Version | Notes |
|---|---|---|---|---|
| coreboot Version | Yes | Included in the build | 4.18 revision dcc5f2e2 | |
| ME firmware | Yes | Proprietary - Not Included | Based on 14.0.47.1558 | |
| Flash Descriptor | Yes | Included in build | ||
| Microcode | Yes | Included in build | Intel Microcode | |
| FSP | Yes | Pulled from Intel github | CometLake | Intel FSP |
| Bootspalsh | Yes | Included in build | N/A | Protectli Splash Screen |
| Video BIOS | No | N/A | N/A | |
| Video boot table (VBT) | Yes | Included in build | ||
