Have a Question?
How to Install the WiFi Kit into the Vault
Overview
Protectli offers an optional WiFi kit that can be used with the Vault. This article will explain how to install the kit into the Vault and how to configure it with one of the supported applications. The SKU for the WiFi Kit is WAP01K.
NOTE: This wireless card is non-standard, in that while it is the PCIe form factor, the electrical connection is via USB. This card is not compatible with the VP series of Vault. Further information on WiFi compatibility can be found here.
Contents
The WiFi Kit contains the following pieces:
- 1 WiFi Card
- 1 Extension Plate
- 2 Screws to connect the Card to the Plate
- 2 Micro Coax Cables with Nuts and Washers
- 2 Antennas
See the photo below for the contents
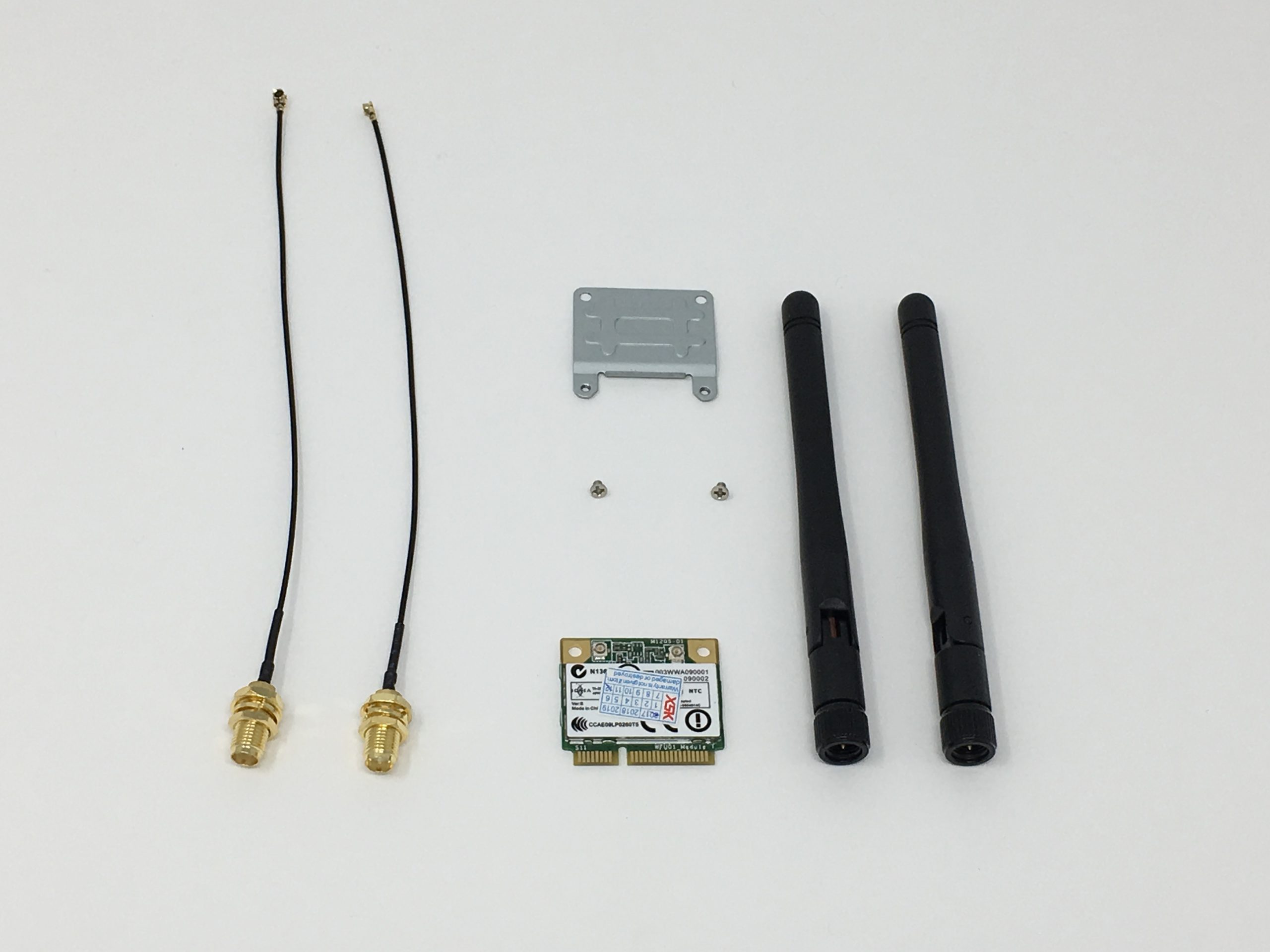
WiFi Kit Contents
WiFi Card Slot
The WiFi Card installs into a PCIe form factor slot in the Vault and is screwed into the existing standoff. The 2 and 4 port Vaults require an extension plate to be connected to the card. The memory for the FW2B and FW4B is below WiFi socket, therefore, memory must be installed before the WiFi card is installed. The 6 port Vault does not require an extension plate, but it is positioned in the chassis underneath the mSATA slot. Therefore, it will need to be inserted before the mSATA. See the photos below for the WiFi card slots.
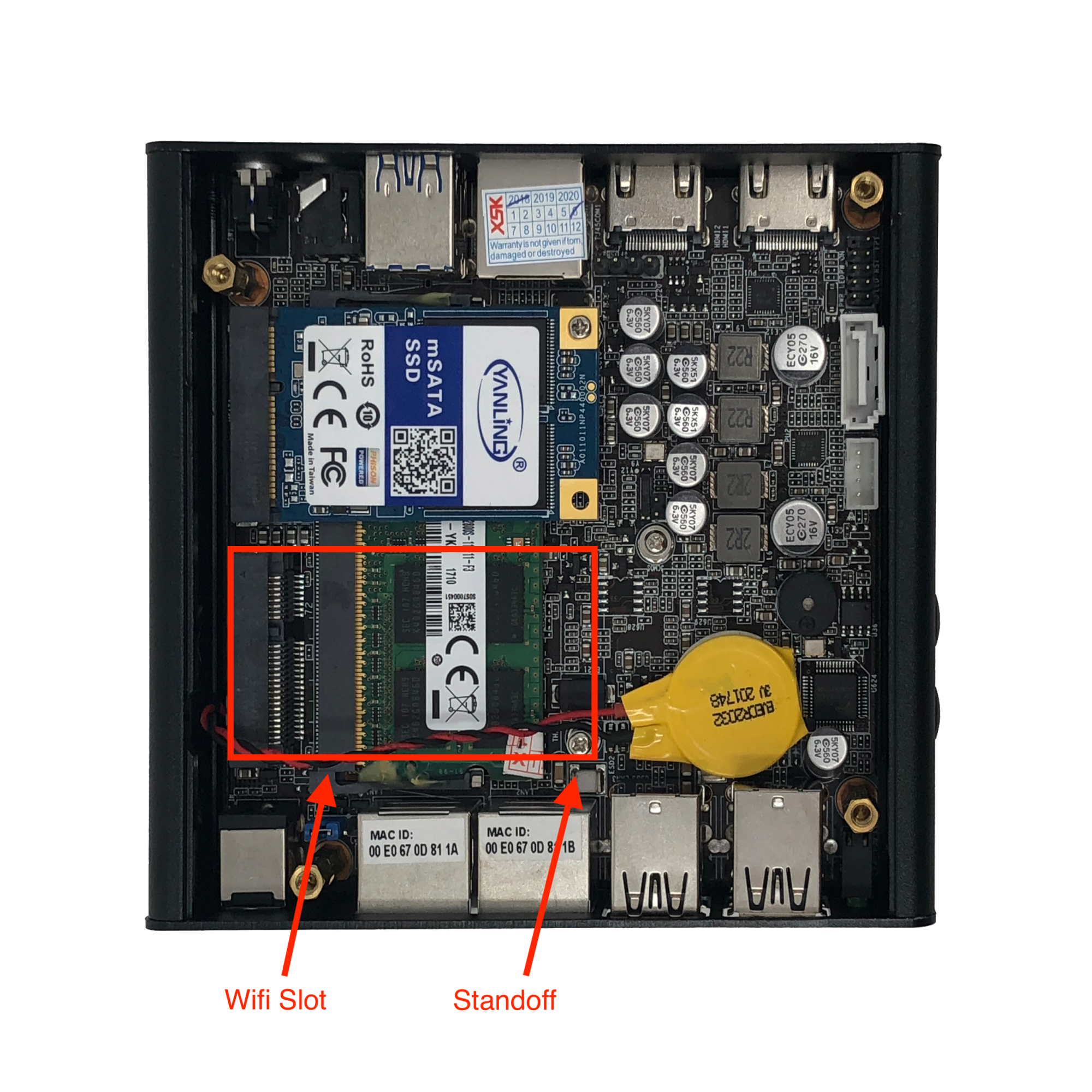
WiFi Slot, FW2B, FW4B
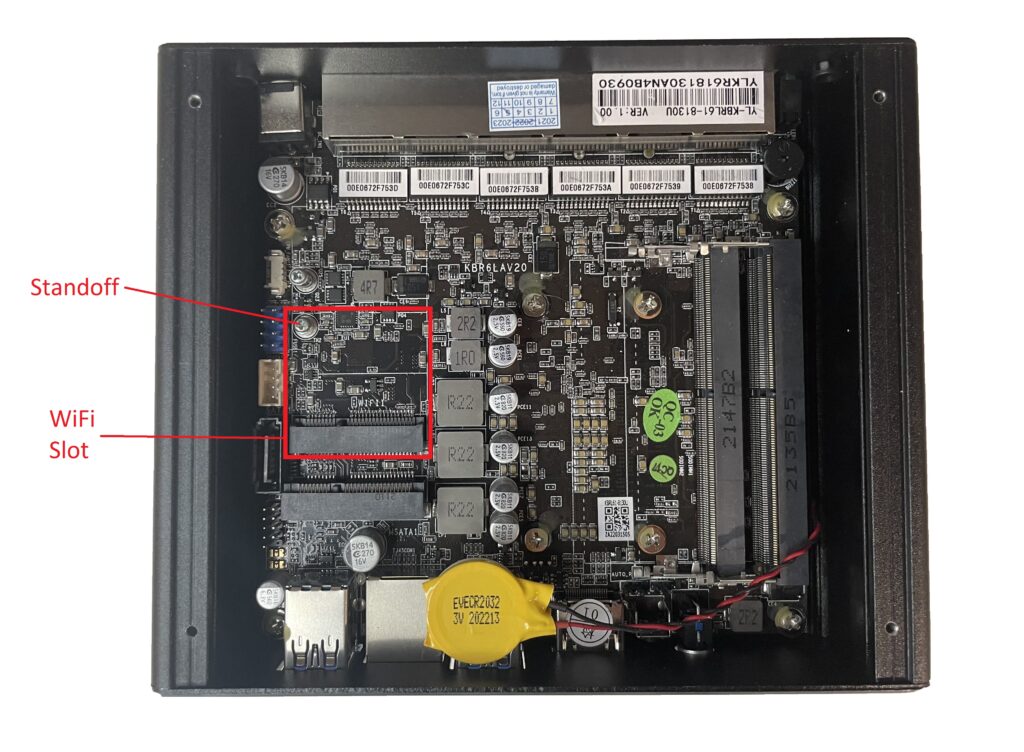
WiFi Slot, FW6
Extension Plate Assembly
As mentioned above, the 2 and 4 port Vaults require an extension plate to be connected to the WiFi card for proper installation. The extension plate is attached to the WiFi card using the 2 small screws in the kit. The screws should be assembled from the top side of the WiFi card and screwed into the threaded holes in the extension plate. See the photo below. The WiFi card can now be inserted into the slot and secured by the screw that comes in the standoff.

WiFi Card and Extension Plate
Install the Antennas
The Antenna Connectors are on the other end of the micro coax cable. The Vault has plastic plugs than can be removed to accommodate the antenna connectors. The plugs can be pushed out using a small screw driver. The location of the plugs on the 2 port and 4 port Vaults is on the side of the chassis. Note that the holes are not completely circular. The top of the hole is flat and the top of the connector is flat so that the connector does not rotate. When inserting the connector into the hole, verify that the flat sides line up.
- Remove the screw and lock washer from the connector
- Insert the connector through the hole with the flat side at the top
- Attach the lock washer and screw to the connector from the outside of the chassis
- The Micro Coax cables attach to the WiFi card. The circular micro coax connectors can be seen in the previous photo at the top of the card near the screws. The photo below shows the coax cables connected to the WiFi card.
- Verify there are no sharp bends in the cable
See the photos below.

Micro Coax Cable Connectors Through Holes in Chassis
Micro Coax Cable Connectors Screwed In
Connect the Antennas
The antennas screw into the connectors that protrude outside the chassis. The photo below shows both antennas in a vertical position, but depending on the network one could be put in the horizontal position for better reception.

Antennas Installed to Chassis

FW4B with WiFi Kit Installed
6 Port Vault Installation
The 6 port Vault installation is slightly different than the 2 and 4 port versions. The 6 port Vault does not require the extension plate. The antenna connector plugs are on the front and clearly marked with the WiFi symbol. The flat side of the antenna connector hole is on the bottom and the WiFi slot is underneath the mSATA slot. The WiFi card must be installed and the micro coax connected to the WiFi card before the mSATA card is installed. Be sure not to pinch the micro coax cable when installing the mSATA card. The photo below shows the 6 port installation before the mSATA is installed above the WiFi card.

6 port Vault WiFi Installation
Configure the WiFi Interface as an Access Point with pfSense® CE
Now that physical hardware has been installed, the WiFi interface must be enabled and configured to operate in the application. Different applications and operating systems will require different configuration procedures. The example below uses pfSense® CE version 2.4.2 to configure the WiFi interface as an Access Point for 802.11G. There is another Knowledge Base article that describes how to install pfSense® CE on the Vault at this link. The information below is specifically to enable the WiFi card and assumes that the user has already successfully installed pfSense® CE on the Vault.
- Browse to an Ethernet port on the Vault in order to access the pfSense® CE Dashboard
- Verify the login page is displayed
- Login and verify that the dashboard page is displayed
- Select Interfaces->Interface Assignments
- Select Wireless
- Add the WiFi interface
- Verify it is "run0(1.0)"
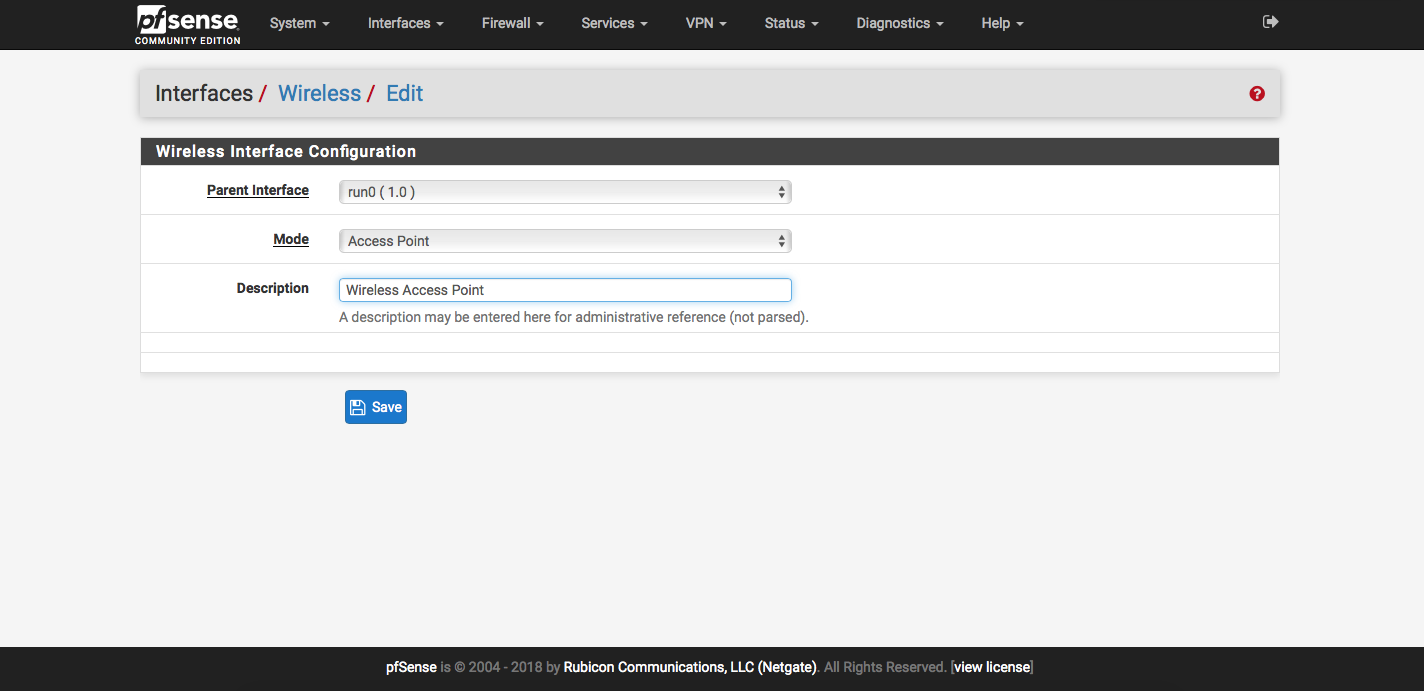
- Set Mode to "Access Point"
- Add Description (optional, recommended)
- Save
- Return to Interfaces->Interface Assignments
- Add the WiFi Interface "run0_wlan0"
- Edit the WiFi interface by hovering over the name in the left column then clicking
- General Configuration
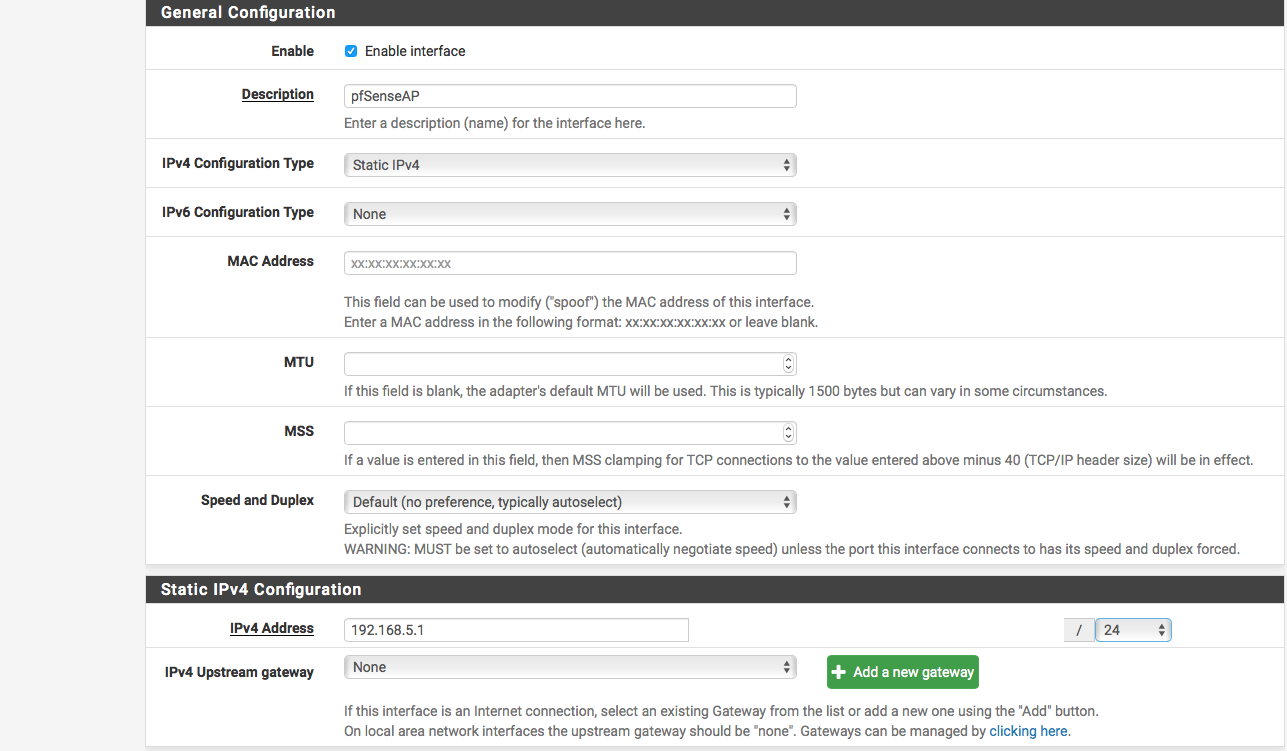
- Enable interface
- IPv4 Configuration Type – Static IPv4
- Static IPv4 Configuration
- IPv4 Address – Enter the desired IP address for the WiFi network, set the subnet mask
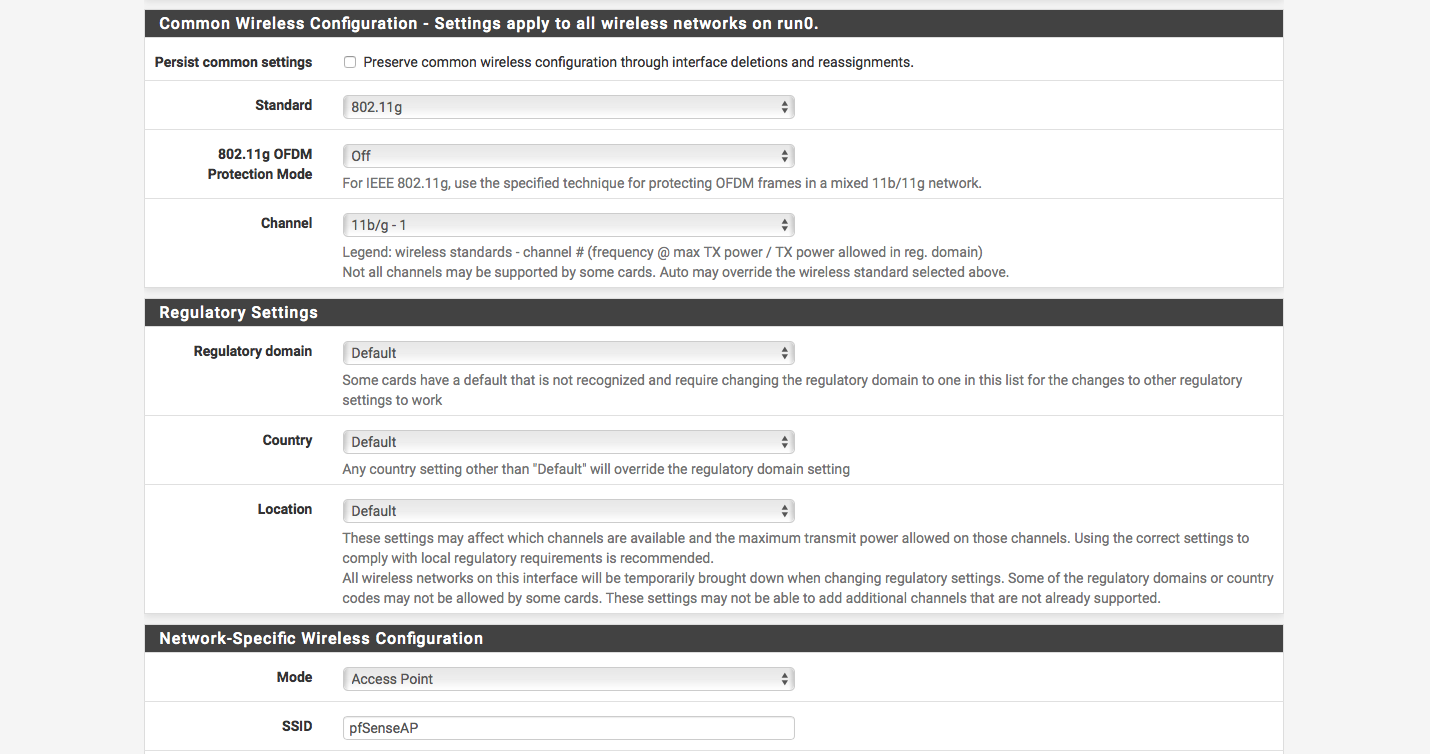
- Common Wireless Configuration
- Standard – 802.11g
- Channel 1
- Network-Specific Wireless Configuration
- Mode – Access Point
- SSID – Set SSID (case sensitive, this is the ID that other clients will use to connect)
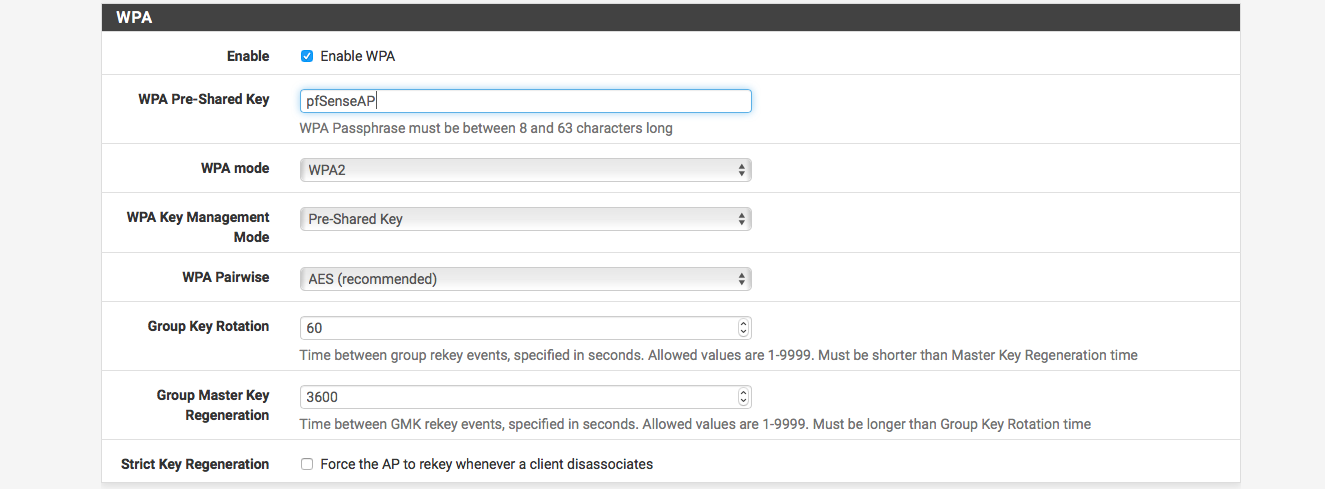
- WPA
- Enable WPA
- WPA Pre-Shared Key – Set key (case sensitive, this is the password that other clients will use to connect)
- Save
- Apply Changes
- Verify the changes have been applied successfully.
As with any other interface, when using pfSense® CE, Services and Firewall rules must be configured in order to connect and pass traffic on the interface. For this example, DHCP server will be configured for the WiFi interface and all traffic will be allowed to pass.
- Go to Services->DHCP Server and select the WiFi interface
- Enable DHCP server, set the DHCP range and Save
- Verify the changes have been applied successfully.
- Go to Firewall->Rules and select the WiFi interface
- Add a Rule to allow traffic to pass
- Save and Apply
- Verify the changes have been applied successfully.
- Verify that another device can connect to the WiFi network that was just created using the SSID and password for the WiFi network.
More details regarding WiFi configuration for pfSense® CE can be found at this link.
Screen shots for the configuration are shown below.
Add Wireless Interface
Set Access Point Mode and Add Description
Enable Wireless Interface and Configure Static IP Address
Configure Wireless Settings
Configure WPA Settings
Configure the WiFi Interface in Infrastructure Mode with FreeBSD
The previous example with the WiFi interface configured it to be an Access Point. An Access Point acts as a communication hub for multiple clients. This example shows how to configure the WiFi interface as a client when the Vault has FreeBSD installed. When configured as a WiFi client, it is referred to as "Infrastructure Mode" or "Base Service Set, (BSS)" There is another article in the Knowledge Base that describes how to install FreeBSD on the Vault at this link. Refer to that article for the basic installation and refer to the instructions below.
During OS installation, in the "Final Configuration" page:
- Select "Network"
- Select "run0" interface
- Select regdomain/country or leave the default to "FCC/US"
- Verify the system scans the wireless networks
- Select the desired network SSID
- Enter the proper password if required for the selected network
- Select Configure IPv4
- Select Configure DHCP
- Select the DNS resolver
- Exit, complete the installation, and reboot
- Verify the FreeBSD boots correctly, wlan interface is present, and can connect to the Wireless network
Performance
The performance of the WiFi on the Vault is is limited to about 10-15 Mbps with pfSense® CE and FreeBSD. Therefore, the WiFi interface should not be used for heavy duty tasks. Its main use is for basic connectivity when fixed Ethernet ports are not available or practical.
If you have any questions, feel free to reach out to us at support@protectli.com, or find more information in our Knowledge Base.