Have a Question?
OPNsense IPSec VPN Performance
The most recent VPN throughput results for OPNsense can be found on this article instead, using the new configuration used in OPNsense 25.1+: https://kb.protectli.com/kb/vpn-performance-results/
OPNsense IPSec VPN Performance
Overview
Depending on individual use cases, different hardware firewalls may be useful for different types of network applications and as such, Protectli offers different hardware with varying capabilities. Frequently, it is useful for a customer to know the performance characteristics of specific hardware before making a decision to purchase. This article aims to provide a baseline of IPSec performance for several different Vaults, as tested in a lab environment, so the customer can make an informed decision as to what products best suit their needs.
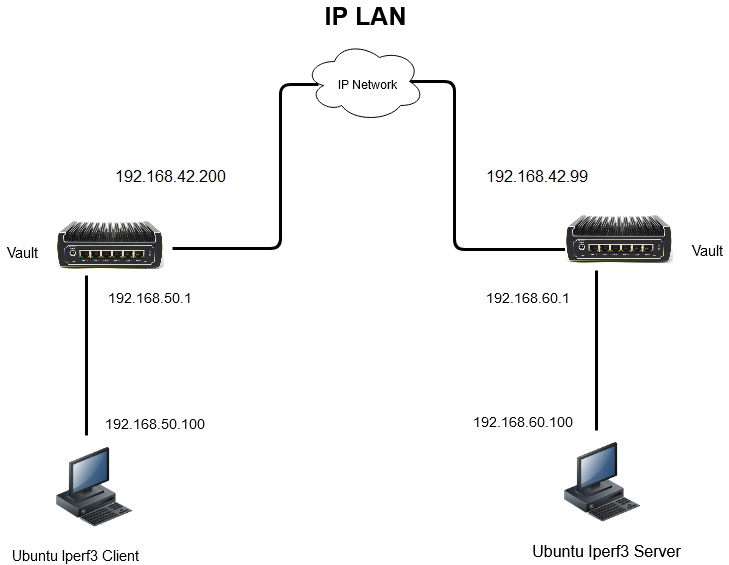
IPSec
When configuring IPsec tunnels (and other secure connections) multiple parameters must be configured. The set of parameters is known as a "cipher suite". The parameters consist of a Key Exchange method, an Encryption method and a Message Authentication method. The configuration must be identical at each end of the tunnel in order to make a connection. An operating system or IPsec implementation will typically support multiple ciphers for each of Key Exchange, Encryption, and Message Authentication that can be combined to form many different cipher suites. OpenSSL, which is an open source software library, provides a large number of ciphers. The list of ciphers supported can be displayed with the command "openssl ciphers –v". The cipher suite is described by combining the methods together into a single string. For example, the cipher DH-RSA-AES256-SHA256 indicates:
Diffie-Hellman (DH) Key Exchange using a Rivest, Shamir, Adelman key (RSA) with
Advanced Encryption Standard 256 bit (AES256) encryption
and Secure Hash Algorithm 256 bit (SHA256) message authentication.There are various standards and recommendations that dictate the required cipher suite for different applications that is beyond the scope of this article.
The diagram below shows an IPsec tunnel. The difference between the LAN example above and the IPsec tunnel is that the entire packet is encrypted "end-to-end" between the Vault/Firewalls and the data can travel through the network securely.
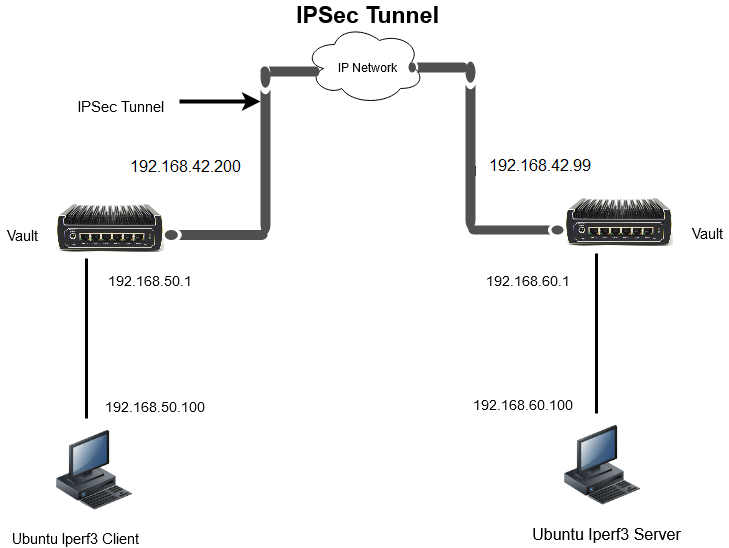
IPSec Performance
Adding an IPSec tunnel introduces "overhead" which is added when a packet enters a tunnel and stripped off when a packet leaves the tunnel. This process adds additional data to each packet, but is not part of the payload. Therefore, when running performance measurement tests, the indicated traffic throughput will be less than throughput achieved without an IPSec encrypted tunnel. In addition to the pure impact on the payload due to additional overhead, the device that adds the overhead must also encrypt the data. Similarly, the device at the other end of the tunnel receiving the packet must decrypt the data before sending it onward. Encryption and decryption of the packet requires significant processing power and affects the throughput of the devices. All current Vault and Vault Pro models include Intel’s AES-NI hardware support which facilitates faster encryption/decryption with less impact on CPU performance. The performance varies depending on the parameters of the many different cipher suites. For example, a cipher suite that uses AES128 may perform better than AES256 due to easier encryption/decryption. It would be difficult if not impossible to test all possible cipher suites. For this purpose, we tested two specific configurations, including one that may not be optimal in terms of performance. On all configurations we tested, we ensured that hardware checksum offload was disabled. This can be found in Interfaces>Settings in the OPNsense WebGUI. In order to test performance, OPNsense 23.7.5 was installed on the Vaults and IPsec tunnels were configured with the following cipher suites:
Configuration 1:
Phase 1: Mutual PSK Authentication Method, AES 256 Encryption Algorithm, SHA512 Hash Algorithm + 14 (2048 bits) DH Key Group
Phase 2: ESP Protocol + AES256 Encryption Algorithm, SHA512 Hash Algorithm + 14 (2048 bits) PFS Key Group
Configuration 2:
Phase 1: Mutual PSK Authentication Method, 128 bit AES-GCm with 128 bit ICV Encryption Algorithm, AES-XCBC Hash Algorithm + 14 (2048 bits) DH Key Group
Phase 2: ESP Protocol + AES128gcm16 Encryption Algorithm, No Hash Algorithm Selected + 14 (2048 bits) PFS Group
Out of these two configurations, configuration 2 would realistically offer faster speeds due to utilizing a less intensive encryption algorithm. With some Vault models, specifically the VP4600 series, setting NAT Traversal (NAT-T) to "Force" in the Phase 1 settings would effectively double throughput performance. If you are seeing slower than expected speeds, please try enabling this.
Observed Throughput Speeds
The results of the performance tests are shown in the table below. Please refer to the exact configurations used in the section above. The throughput averages are results from an iPerf3 test that ran for 5 minutes with four (4) parallel streams. Results in the real world may vary depending on variables such as distance between VPN sites, ISP speeds, and other network hardware conflicting with the IPSec traffic.
For more detailed information on the performance results, please click on this link: OPNsense IPSec Performance
| Vault Model | Config 1 Throughput Average (AES 256, SHA512, 14 [2048 bits] DH, ESP, AES256, SHA512 + 14 [2048 bits] PFS | Config 2 Throughput Average (128 bit AES-GCM with 128 bit ICV, AES-XCBC, 14 [2048 bits] DH, ESP, AES128gcm16, No Hash,14 [2048 bits] PFS) | OS Version |
|---|---|---|---|
| FW2B | ~202 Mbps | ~529 Mbps | 23.7.5 |
| FW4B | ~202 Mbps | ~747 Mbps | 23.7.5 |
| FW4C | ~235 Mbps | ~807 Mbps | 23.7.5 |
| VP2410 | ~319 Mbps | ~809 Mbps | 23.7.5 |
| VP2420 | ~380 Mbps | ~1320 Mbps | 23.7.5 |
| VP2430 | ~684 Mbps | ~2060 Mbps | 25.1 |
| FW6A | ~250 Mbps | ~785 Mbps | 23.7.5 |
| FW6Br2 | ~501 Mbps | ~814 Mbps | 23.7.5 |
| FW6C | ~468 Mbps | ~821 Mbps | 23.7.5 |
| FW6D | ~514 Mbps | ~879 Mbps | 23.7.5 |
| FW6E | ~521 Mbps | ~879 Mbps | 23.7.5 |
| VP4630 | ~675 Mbps | ~1790 Mbps (NAT-T On), ~870 Mbps (NAT-T Off) | 23.7.5 |
| VP4650 | ~648 Mbps | ~1910 Mbps (NAT-T On), ~860Mbps (NAT-T Off) | 23.7.5 |
| VP4670 | ~680 Mbps | ~2200 Mbps (NAT-T On), ~875 Mbps (NAT-T Off) | 23.7.5 |
| V1610 | ~701 | ~2.02Gbps | 24.7 |
Conclusions
IPsec is a critical set of protocols used to provide secure communication through the Internet. There are many different cipher suites that can be used depending on the requirements of the user. The configuration used may impact the performance and therefore the throughput of the devices in the network. This tutorial is an aid to selecting the best Vault for your application. If you have any questions, feel free to reach out to us! You can submit a ticket here, find more information in our Knowledge Base, or visit the pages at IETF as reference.
