Have a Question?
[New] VPN Performance Results (Wireguard, IPSec, OpenVPN)
Introduction
TL;DR: This article was made to provide expected VPN throughput on every Vault product when configured in a site-to-site configuration, for every kind of VPN protocol (tested on OPNsense). Scroll down to the VPN Throughput Results section to view the numbers.
A VPN (Virtual Private Network) establishes an encrypted connection between a device and a remote server over a public or untrusted network. It enables secure transmission of data by encapsulating network traffic, masking the user's IP address, and maintaining privacy and integrity across the connection. These can also be used to remotely connect to remote office locations for businesses.
There are two major types of VPN connections: client-based VPNs (commonly used with VPN providers) and site-to-site VPNs.
In client-based VPNs, individual users connect to a remote VPN server operated by a provider such as Proton VPN, NordVPN, or Mullvad VPN, to name a few. The connection is typically established using protocols like OpenVPN, WireGuard, or IKEv2/IPsec, which handle authentication, encryption, and tunnel negotiation. These VPN clients can be run directly on an endpoint device (e.g., a laptop or smartphone) or configured manually on network appliances or firewalls like OPNsense or pfSense®, allowing all devices behind that firewall to use the tunnel.
In a site-to-site VPN, two networks, typically each protected by a firewall, are connected securely over the internet. Each site uses a public IP address to establish a persistent encrypted tunnel to the other. This setup allows devices on either network to communicate with each other as if they were on the same local network. Site-to-site VPNs are often configured using IPsec, OpenVPN, or WireGuard, and are commonly used for secure communication between branch offices or data centers.
VPN performance is a popular metric used to determine what kind of Protectli Vault product may work for you. Typically, more powerful CPUs will be able to provide higher throughput on a VPN connection. Data throughput on a VPN connection will inherently be lower than unencrypted traffic due to the computational overhead introduced by encryption and encapsulation processes. Each packet must be encrypted and decrypted in real-time, which consumes CPU resources, especially with protocols like OpenVPN, which are single-threaded and CPU-intensive. Additionally, the type of encryption algorithm used (e.g., AES-256 vs ChaCha20), the VPN protocol, and whether the device supports hardware acceleration for cryptographic operations (such as AES-NI) can all significantly impact VPN throughput. This article is made to provide expected VPN throughput on every Vault product when configured in a site-to-site configuration, for every kind of VPN protocol. Real world results can vary, and this should also assist with "guestimating" what kind of throughput speeds you may get with a VPN provider.
The Setup Used
To test throughput on every VPN connection on every Vault, we used a specific setup to maintain consistency between tests. coreboot firmware was utilized on every Protectli Vault in the setup.
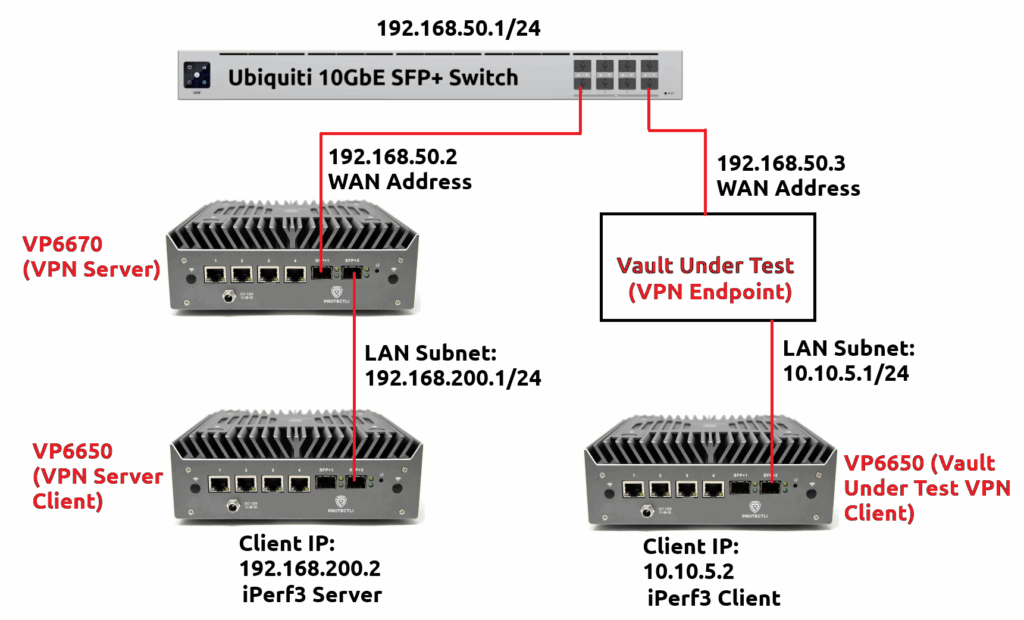
A VP6670 with 32GB of RAM was utilized as one firewall endpoint (the main server), and the operating system in test (OPNsense) was installed to an NVMe drive. This unit was provided a static WAN address on a local network connected to a Ubiquiti 10GbE Switch. The LAN interface was configured with an IP of 192.168.200.1/24.
The device under test (the client VPN) was used as the other firewall endpoint, typically using 32GB of RAM unless the maximum amount of RAM allowed was less than that (for example, the VP2410 supports a maximum of 16GB of RAM). The OS in test was installed to an NVMe or a supported M.2 or mSATA SSD if NVMe was not supported on the device. This device was given a static WAN address on a local network connected to a Ubiquiti 10GbE switch. The LAN interface was configured with an IP of 10.10.5.1/24.
Both of these firewall endpoints had an individual VP6650 connected to the LAN port to act as clients. These clients have Ubuntu 24.04 installed to an NMVe drive and contain 32GB of RAM. The client connected to the main server (the VP6670) would run an iPerf3 server. The client connected to the device under test would be acting as an iPerf3 client. Throughput was recorded over a 60 second test using the command: iPerf3 -c [Server IP] -P4 -t60
An image outlining the setup can be seen below:
VPN Throughput Results
Please remember that our throughput results may slightly differ from what you see in your setup or in other real-world scenarios. As these are average speeds over a small period of time, you certainly may see higher or lower speeds when passing traffic in your setup at any given time. These results should provide a solid expected baseline.
Wireguard
Configured via the Wireguard plugin on OPNsense. Configured by generally following the instructions on OPNsense's documentation.
The WireGuard implementation on OPNsense is fairly straightforward without many configurable options. WireGuard utilizes the ChaCha20Poly1305 cipher suite.
| Vault Model | Throughput Results | OPNsense Version |
|---|---|---|
| V12XX/V14XX | 2.18 Gbps (2180 Mbps) | 25.7 |
| V16XX | 2.24 Gbps (2240 Mbps) | 25.7 |
| VP2410 | 900 Mbps | 25.7 |
| VP2420 | 2.24 Gbps (2240 Mbps) | 25.7 |
| VP2430 | 2.25 Gbps (2250 Mbps) | 25.7 |
| VP2440 | 4.15 Gbps (4150 Mbps) | 25.7 |
| VP3210 | 2.25 Gbps (2250 Mbps) | 25.7 |
| VP3230 | 2.25 Gbps (2250 Mbps) | 25.7 |
| VP4630 | 2.25 Gbps (2250 Mbps) | 25.7 |
| VP4650 | 2.25 Gbps (2250 Mbps) | 25.7 |
| VP4670 | 2.25 Gbps (2250 Mbps) | 25.7 |
| VP6630 | 4.8Gbps (4800 Mbps) | 25.7 |
| VP6650 | 4.6 Gbps (4600 Mbps) | 25.7 |
| VP6670 | 5.01 Gbps (5010 Mbps) | 25.7 |
| FW2B | 280 Mbps | 25.7 |
| FW4B | 290 Mbps | 25.7 |
| FW4C | 315 Mbps | 25.7 |
| FW6A | 876 Mbps | 25.7 |
| FW6Br2/C/D/E | 905 Mbps | 25.7 |
IPSec
When configuring IPsec tunnels (and other secure connections) multiple parameters must be configured. The set of parameters is known as a "cipher suite". The parameters consist of a Key Exchange method, an Encryption method and a Message Authentication method. The configuration must be identical at each end of the tunnel in order to make a connection. An operating system or IPsec implementation will typically support multiple ciphers for each of Key Exchange, Encryption, and Message Authentication that can be combined to form many different cipher suites. OpenSSL, which is an open source software library, provides a large number of ciphers. The list of ciphers supported can be displayed with the command "openssl ciphers –v".
With the release of OPNsense 25.7, the "legacy" IPSec connections were removed and completely replaced with new configuration methods. These new configuration methods are relatively easier to configure, and all of our tests were performed by following these set of instructions from OPNsense's official documentation. We used two different proposals to test expected throughput, as seen below:
Configuration 1:
Proposal: AES256-SHA512-modp2048 [DH 14]
Version: IKEv1+IKEv2
Configuration 2:
Proposal: AES128-AESXCBC-modp2048 [DH 14]
Version: IKEv1+IKEv2
| Vault Model | Config 1 Results | Config 2 Results | OPNsense Version |
|---|---|---|---|
| V12XX/V14XX | 1.98 Gbps (1980 Mbps) | 1.98 Gbps (1980 Mbps) | 25.7 |
| V16XX | 1.98 Gbps (1980 Mbps) | 1.87 Gbps (1870 Mbps) | 25.7 |
| VP2410 | 888 Mbps | 890 Mbps | 25.7 |
| VP2420 | 1.99 Gbps (1990 Mbps) | 1.99 Gbps (1990 Mbps) | 25.7 |
| VP2430 | 2.25 Gbps (2250 Mbps) | 2.25 Gbps (2250 Mbps) | 25.7 |
| VP2440 | 3.64 Gbps (3640 Mbps) | 3.85 Gbps (3850 Mbps) | 25.7 |
| VP3210 | 1.92 Gbps (1920 Mbps) | 1.95 Gbps (1950 Mbps) | 25.7 |
| VP3230 | 2.00 Gbps (2000 Mbps) | 1.99 Gbps (1990 Mbps) | 25.7 |
| VP4630 | 2.19 Gbps (2190 Mbps) | 2.16 Gbps (2160 Mbps) | 25.7 |
| VP4650 | 1.98 Gbps (1980 Mbps) | 1.98 Gbps (1980 Mbps) | 25.7 |
| VP4670 | 1.98 Gbps (1980 Mbps) | 1.95 Gbps (1950 Mbps) | 25.7 |
| VP6630 | 3.05 Gbps (3050 Mbps) | 3.02 Gbps (3020 Mbps) | 25.7 |
| VP6650 | 3.82 Gbps (3820 Mbps) | 3.84 Gbps (3840 Mbps) | 25.7 |
| VP6670 | 4.30 Gbps (4300 Mbps) | 4.05 Gbps (4050 Mbps) | 25.7 |
| FW2B | 200 Mbps | 530 Mbps | 25.1 |
| FW4B | 200 Mbps | 700 Mbps | 25.1 |
| FW4C | 235 Mbps | 800 Mbps | 25.1 |
| FW6A | 250 Mbps | 780 Mbps | 25.1 |
| FW6Br2/C/D/E | ~500 Mbps | ~850 Mbps | 25.1 |
OpenVPN
OpenVPN is a popular protocol that is used to authenticate and encrypt/decrypt packets to provide secure transport of packets through the network. An OpenVPN "tunnel" encrypts the entire packet, not just the payload. OpenVPN connections are typically much slower than a Wireguard or IPSec connections due to it's somewhat dated design.
With the introduction of OPNsense 25.7, the older method of configuring OpenVPN connections has been removed. The only available option is to configure an OpenVPN connection via the new "Instances" method (SSL VPN Site to Site). This requires you to setup a tunnel on both ends, and you must configure certificates to warrant trust between both machines. You need a root CA that issues two leaf certificates, one for each site (server and client). To configure this, we followed OPNsense's official documentation.
The only major variable we can change to potentially affect throughput speed is the Data Cipher utilized. This can be configured on the OpenVPN server settings between AES-256-GCM, AES-128-GCM, or CHAHCA20-Poly1305. For these tests, we recorded results for each data cipher.
| Vault Model | AES-256-GCM | AES-128-GCM | CHACHA20-Poly1305 | OPNsense Version |
|---|---|---|---|---|
| V12XX/V14XX | 1.02 Gbps (1020 Mbps) | 976 Mbps | 816 Mbps | 25.7 |
| V16XX | 1.07 Gbps (1070 Mbps) | 1.09 Gbps (1090 Mbps) | 892 Mbps | 25.7 |
| VP2410 | 475 Mbps | 416 Mbps | 358 Mbps | 25.7 |
| VP2420 | 681 Mbps | 620 Mbps | 527 Mbps | 25.7 |
| VP2430 | 1.10 Gbps (1100 Mbps) | 1.12 Gbps (1120 Mbps) | 994 Mbps | 25.7 |
| VP2440 | 1.10 Gbps (1100 Mbps) | 1.12 Gbps (1120 Mbps) | 994 Mbps | 25.7 |
| VP3210 | 950 Mbps | 912 Mbps | 865 Mbps | 25.7 |
| VP3230 | 1.11 Gbps (1110 Mbps) | 1.03 Gbps (1030 Mbps) | 1.02 Gbps (1020 Mbps) | 25.7 |
| VP4630 | 1.01 Gbps (1010 Mbps) | 1.02 Gbps (1020 Mbps) | 801 Mbps | 25.7 |
| VP4650 | 999 Mbps | 985 Mbps | 890 Mbps | 25.7 |
| VP4670 | 1.04 Gbps (1040 Mbps) | 1.02 Gbps (1020 Mbps) | 798 Mbps | 25.7 |
| VP6630 | 1.13 Gbps (1130 Mbps) | 1.10 Gbps (1100 Mbps) | 945 Mbps | 25.7 |
| VP6650 | 1.06 Gbps (1060 Mbps) | 939 Mbps | 861 Mbps | 25.7 |
| VP6670 | 1.05 Gbps (1050 Mbps) | 881 Mbps | 871 Mbps | 25.7 |
| FW2B | 100 Mbps | 105 Mbps | 98 Mbps | 25.7 |
| FW4B | 175 Mbps | 180 Mbps | 149 Mbps | 25.7 |
| FW4C | 219 Mbps | 190 Mbps | 180 Mbps | 25.7 |
| FW6A | 730 Mbps | 735 Mbps | 485 Mbps | 25.7 |
| FW6Br2/C/D/E | ~750 Mbps | ~750 Mbps | ~600 Mbps | 25.7 |
Conclusion
If you have any questions, feel free to reach out to us at support@protectli.com
All of the Protectli Vaults outlined in this article can be purchased directly from Protectli.com or our Amazon storefront.
